Ranch Networks Configuration for MIDCOM Link with IP-PBX Asterisk
Preface
Ranch Networks devices provide many features at a competitive price, that makes them perfect candidates to border firewall solutions. In its core, “zone” ideology is used, allowing physical ports and VLAN-tagged connections be firewalled independently between each other. In addition to static firewall rules, Ranch Networks devices support MIDCOM protocol for dynamic firewall handling. Asterisk controls Ranch Network devices via libmidcom library. Ranch Networks devices can also “re-invite” SIP RTP traffic for passing through internal “VoIP bridge” between zones.
1. Initial Assumptions
Assuming Asterisk is latest stable asterisk-1.2.x-netsec version.
Assuming Ranch Networks device has a VoIP-enabled firmware.
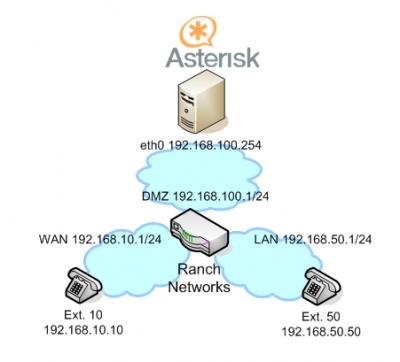
Assuming RN configuration for following network topology:
DMZ 192.168.100.1/24
LAN 192.168.50.1/24
WAN 192.168.10.1/24
Asterisk in DMZ zone, 192.168.100.254
Phones in LAN and WAN zones
LAN Phone (Ex.50): 192.168.50.50
WAN Phone (Ex. 10): 192.168.10.10
2. Enabling MIDCOM. libmidcom configuration, compilation and running
Download the NETSEC library libmidcom-0.1.0.tar.gz from: http://ftp.digium.com/pub/asterisk
Untar and compile NETSEC to any folder, i.e. /usr/src/
Edit Makefile /usr/src/libmidcom-0.1.0/midcom/Makefile :
replace:
DEFS = -DEXTENDED_SIMCO #-DNO_SSL
with:
DEFS = -DEXTENDED_SIMCO -DNO_SSL
Stop Asterisk.
Make-install libmidcom.
Recompile Asterisk.
Revise /etc/asterisk/modules.conf:
make sure that string:
insert load=res_netsec.so
is located BEFORE then:
insert chan_sip.so
Arrange them in correct order if needed.
Create (or edit) /etc/asterisk/midcom.conf . Example shown is for assumed network topology, with default RN username and password, and source code dir in /usr/src/:
[general]
midcomnat = farend ; farend, for Far-end NAT
; nearend, for Near-end NAT
; no, if midcom is not required (default)
certificate = /usr/src/libmidcom-0.1.0/midcom/server.pem
; Path to the stored certificate for this midbox
lb = rrobin ; Load blancing alg used to select Far-end firewalls
[firewallA]
type = MIDBOX
ip = 192.168.100.1 ; IP address of the midbox
username = root ; username for authentication
password = ranchroot
transport = PLAIN ; PLAIN for plain-text, TLS for encryption
mode = farend ; farend for Far-end NAT, nearend for Near-end NAT
Start Asterisk
3. Ranch Networks device configuration.
3.1. Setting “ACCEPT-ALL” policy for WAN, LAN and DMZ.
For initial setup and test, it is recommended to set “ACCEPT-ALL” policies for all physical and virtual zones involved.
Open Firewall Configuration -> Security Profiles
Select “LAN” in drop-down list of Firewall Rules for Security profiles.
Make Sure the Default Rule ID 65535 denies any traffic at any circumstance in this zone
Add a new rule, i.e. ID 222, that would accept all traffic in this zone, save the newly added rule.
Repeat this steps for all zones involved into setup (i.e. DMZ, WAN).
Revise all “ACCEPT-ALL” rules for errors.
Save running configuration.
3.2. Configuring Virtual IP for SIP RTP “re-invitation”
Open Load Balancing -> Switching Configuration -> Virtual IP Configuration
Add new Virtual IP address, i.e. from DMZ zone, that will be used for SIP RTP “re-innvitation”
192.168.100.253 “Virtual IP for VoIP bridging”
3.2. Enabling dynamic firewall re-configuration
Go to Firewall Configuration -> MIDCOM Configuration
Select zones where “VoIP” will be enabled. “VoIP enabled” means that RN device will support the media stream (for example RTP) in this particular zone. Because RN devices control only the traffic
that is going out from the secure zone, the only zones that consist of the VoIP phones should be “VoIP enabled”.
Add Dynamic NAT configuration as “One NAT for all IP addresses”:
192.168.100.253
“One-NAT-for-ALL” means that all phones will be “nated” to the virtual IP address – which is the IP Address of the RTP bridge ( inside RN ). The Virtual IP address should be selected from the secure zones subnets that is reachable from the all phones location. For example: if you have the phones that are deployed inside (in the private network) as well as outside (public internet ) the virtual IP Address for the VoIP should be selected from the public ranch of the IP Addresses.
3.3 Configuring NAT between RN zones
For this example the NAT on Ranch Networks device should be
configured as follows :
LAN to -> DMZ NO-NAT
WAN to -> DMZ NO-NAT
DMZ to LAN and WAN NO-NAT
Save running configuration and reboot device.
4. Sample /etc/asterisk/sip.conf
[50]
type=friend
host=dynamic
callerid=TEST <50>
username=50
mailbox=50
dtmfmode=inband
context=local
qualify=yes
nat=no
[10]
type=friend
host=dynamic
callerid=TEST <10>
username=50
mailbox=50
dtmfmode=inband
context=local
qualify=yes
nat=no
5. Testing
No advices. Testing is testing. There is a Syslog client in each RN device, this helps.
6. Setting “ACCEPT SIP” policy on Ranch Networks device
After you have all tests done, simply edit “ACCEPT-ALL” firewall rules from 3.1.:
Firewall Configuration -> Security Profiles
Choose appropriate zone and rule -> Add/Modify
In rule config window, open “Source port” link -> List -> Type in 5060 in the text box under list of different protocols -> OK.
Select “UPD” in protocol drop-down menu.
Please note: the DMZ zone ( or any secure zone) should not be the firewall free,
however at least the UDP traffic on the port 5060 should be enabled from DMZ to the phones zones.