Page Contents
- Overview
- Fraud Phone Number Database
- Hacker IP Address Database
- Geographic IP Database
- Brute Force Attack Detection
- Breached Credential Use Detection
- Heuristic Attack Detection
- Dial Pattern Recognition
- Trunk and Endpoint Trust
- Threat Level Management
- Telnet Interface
- Browser Interface
- Socket & REST Interfaces
- Asterisk Compatibility
- Manufacturer
- Screenshots
Overview
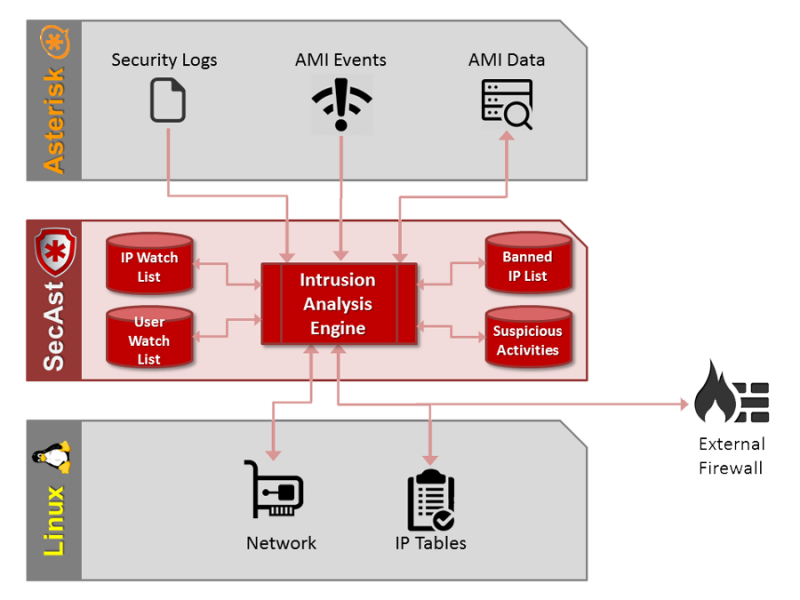
SecAst is a fraud and intrusion detection and prevention system designed specifically to protect Asterisk based phone systems. SecAst uses a variety of techniques and proprietary databases to detect intrusion attempts, halt ongoing attacks, and prevent future attacks. In addition, SecAst uses advanced techniques to detect valid credentials that have been disclosed / compromised and are being abused, and uses heuristic algorithms to learn attacker behaviour. Upon detection of fraud or attack SecAst can disconnect calls and/or block the attacker from Asterisk at the network level.
SecAst offers the industry’s largest databases of fraudulent phone numbers and hacker IP addresses, available to both carriers and end-users. Using Telium’s comprehensive fraud & hacker databases allows administrators to mitigate the intrusion risk of known attackers, and reduce the risk of fraudulent toll / premium rate charges.
SecAst offers a proprietary geographic IP address database allowing the administrator to create allow / deny rules (geofencing) down to the city level without large or complex firewall rules (all geofencing rules remain within SecAst). Use of geofencing dramatically reduces the number of, and risk from, attacks allowing administrators to quickly eliminate continents / countries / regions / cities where their users would never be located.
SecAst is a 100% software solution, communicating with a number of Asterisk, network, and Linux subsystems. The data from these sources allows SecAst to monitor connection and dial attempts with invalid credentials, the rate at which users / peers are dialing, the number of channels in use by user / peer across all protocols, the source IP of remote users / peers, etc. By combining this data with Fraud and GeoIP databases SecAst can effectively stop attacks / fraud in its tracks, and alert the administrator with details of each attack.
SecAst offers extensive interfaces to interact with other programs, utilities, external firewalls, billing systems, etc. allowing for considerable customization. For example, changes in Threat Level can trigger scripts which alert administrators, shutdown interfaces, change firewall rules, etc.
SecAst is available in both free and commercial editions. You can get SecAst, as well as more documentation, at www.telium.ca.
Fraud Phone Number Database
SecAst can check every phone number dialed against a database of phone numbers known to be involved in fraud (and hacking) activities. Calls suspected of being fraudulent can be automatically disconnected and/or originating devices can be blocked from connecting to the PBX. SecAst can also treat premium rate and shared cost numbers differently, helping to avoid calls to zero-day fraud number exploits. Telium’s fraud database has been developed over many years and is one of the largest and most comprehensive fraud prevention tools available to carriers and end-users.
Hacker IP Address Database
SecAst can check the source IP address of every device/user agent against a database of IP addresses known to be used in hacking (and fraud) activities. SecAst can also treat proximate addresses (which may be owned by the same hacker) as suspect and evaluate them based on their neighbours. Devices suspected of being involved in hacking can be prevented from making calls and/or blocked from connecting to the PBX. Telium’s hacker database has been developed over many years and is one of the largest and most comprehensive intrusion prevention tools available to carriers and end-users.
Geographic IP Database
SecAst incorporates a database of IPv4 and IPv6 address across the world, including the continent / country / region / city of each IP. SecAst can be configured to allow or deny access to any combination of these geographic attributes (as well as a default allow / deny behavior). If an attacker or user attempts to use the Asterisk server from a denied location, the user is immediately disconnected. This creates a geographic fence (or geofence) which keeps good guys in and bay guys out.
Brute Force Attack Detection
SecAst can detect brute force attacks (attempts to gain access by trying various combinations of usernames/passwords, commonly used extensions, commonly used passwords, etc). Unlike other products, SecAst can detect these attacks even if spread across many days (attackers are now performing “thin” attacks to bypass simplistic detection programs like fail2ban). SecAst can respond to these attacks by blocking them at the network level, preventing any further attempts. These blocks can last for hours, days, or indefinitely.
Breached Credential Use Detection
SecAst can detect unusual traffic and usage patterns indicative of credentials that have been breached (leaked or somehow discovered by an attacker). This includes monitoring the number of calls in progress, how quickly the calls are setup, even the rate at which the user is dialing digits. SecAst can respond to these attacks by blocking them at the network level, preventing any further attempts. These blocks can last for hours, days, or indefinitely.
Heuristic Attack Detection
SecAst can learn new attack patterns and adjust its detection accordingly. The heuristic scanner monitors a variety of Asterisk and network traffic patterns to detect suspicious activity, correlate them with rules which indicate likely attacker activity, and then block the attacker at the network level, preventing any further attempts. These blocks can last for hours, days, or indefinitely.
Spread-IP Detection
SecAst can detect attacks from hackers who are constantly and rapidly changing IP addresses. Professional hackers are now rotating their IP addresses through large ranges of IP addresses from clouds, VPN services, large subnets, etc. to avoid detection by simplistic tools like fail2ban or regular firewalls. SecAst integrates a diverse collection of data points to allow detection of hackers before they can even use a new IP to connect to the PBX.
Dial Pattern Recognition
SecAst monitors all digits being dialed and can block attempts to call restricted numbers. Although dialplans also perform this function, if an Asterisk server is compromised (eg: FreePBX GUI hacked) then SecAst will override the dialplan and still block or accept only certain numbers. Dial pattern recognition can match any dial string and either allow or block the dial attempt based on administrator defined rules.
Trunk and Endpoint Trust
SecAst can be instructed to trust particular trunks, endpoints (users or phones), and IP addresses so that they are exempt from security screening. This allows administrators to grant particular users access regardless of location, call volumes, etc. (which may be necessary for traveling sales staff, etc). This also allows administrators to designate certain trunks / routes as trusted and others as untrusted.
Threat Level Management
SecAst monitors the number and rate of attacks against the Asterisk server, and based on administrator defined thresholds will set the threat level of the system. Changes in threat levels can trigger custom scripts, notifications, and other system based features.
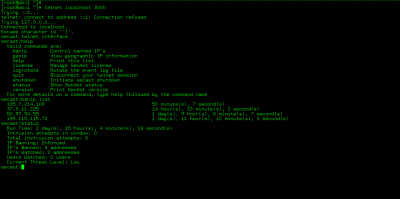
Telnet Interface
Administrators will be immediately comfortable with the simple and powerful telnet interface to SecAst. The security system can be managed and controlled from a telnet interface, whether from a PC, a tablet, or a cell phone. The interface includes online help, and user friendly rich terminal output.
Browser Interface
Seasoned administrators and novices alike will be comfortable with the simple and powerful browser (web) interface to SecAst. The security system can be managed and controlled from any browser, including a PC, a tablet, or a cell phone. The interface includes blocking / unblocking IP’s, checking threat levels, viewing attack history, etc.
Socket & REST Interfaces
Developers will appreciate the socket and REST (Representational State Transfer) interfaces to SecAst, as the power and control of SecAst can be easily expanded and integrated with other system administration and monitoring tools. SecAst includes sample PHP code to show how to extract data and control SecAst via a web service and via the socket interface.
Asterisk Compatibility
SecAst is compatible with a broad range of Asterisk versions and distributions. SecAst works with Asterisk versions 1.4 through 16, both 32-bit and 64-bit. SecAst is also compatible with a wide range of Asterisk distributions, from Digium’s plain old Asterisk, to FreePBX and PBX In A Flash and TrixBox, to 3rd Lane and more. SecAst is also the only product to work across multiple protocols/modules including PJSIP,SIP,IAX,IAX2,MGCP (and more).
Manufacturer
SecAst is produced by Telium:
Web: www.telium.io
Tel: (519) 266-4357
E-Mail: [email protected]
Screenshots
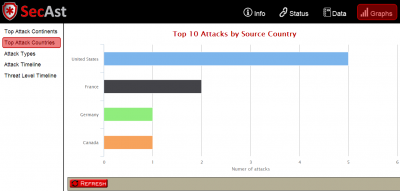
Web Interface – Top attack sources by country
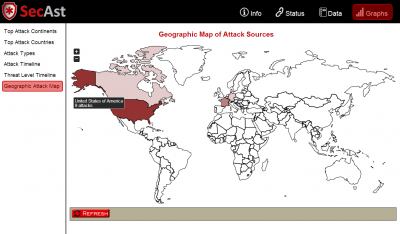
Web Interface – Map of attack sources
E-Mail Interface – Attack alert
Telnet Interface – Control by telnet